If you are using an existing VoIP user then you must be aware that Voice over Internet Protocol (VoIP) services come with certain risks that can compromise the security and reliability of your VoIP system.
In this blog, we will explore ten common vulnerabilities found in VoIP systems and outline effective countermeasures to protect your communications.
Whether you are new to VoIP or looking to improve your existing setup, understanding these vulnerabilities and how to address them is crucial for ensuring a secure and dependable VoIP experience.
What is security in VoIP?
Security in VoIP includes the strategies and actions implemented to protect voice communications that are transmitted over internet protocol networks from interception, disruption, or misuse. Similar to traditional telephony, VoIP must be secured to ensure the confidentiality and availability of communications.
10 VoIP Vulnerabilities and Countermeasures
1/ Eavesdropping:
Eavesdropping is a significant threat in VoIP communications, where unauthorized individuals can intercept and listen to your conversations without permission.
This vulnerability occurs because VoIP calls are transmitted over the internet in data packets, which can be intercepted using techniques like packet sniffing.
Attackers can exploit unsecured networks, weak encryption, or hacked devices to get access to these packets, thereby getting your sensitive information such as personal details, business plans, and confidential discussions. As per the data, over 37% of smartphones worldwide could be targeted for eavesdropping.
To counteract eavesdropping, you must implement strong encryption protocols like Secure Real-time Transport Protocol (SRTP) and Transport Layer Security (TLS).
These protocols help secure your data packets by encrypting them during transmission, thus significantly reducing the chances of unauthorized parties intercepting and decoding your communications.
Additionally, you should regularly update your VoIP software, use Virtual Private Networks (VPNs) to secure connections, and conduct routine security audits to identify and reduce potential vulnerabilities.
2/ Denial of Service (DoS) Attacks:
Denial of Service (DoS) attacks present a significant risk to VoIP systems by flooding the network with an unusually high volume of traffic, which disrupts your regular communication processes.
During a DoS attack, your VoIP services can become slow or completely unavailable, which critically impacts productivity and can potentially lead to significant financial losses.
Attackers achieve this by flooding your network with illegitimate requests, thus consuming your system’s resources and preventing legitimate users from making or receiving calls.
To protect against DoS attacks, strong network security protocols are crucial. You can begin by installing firewalls and intrusion prevention systems (IPS) capable of identifying and blocking harmful traffic.
Ensure your VoIP infrastructure has backup and load-balancing configurations to distribute traffic loads evenly, stopping any single point from becoming overloaded.
Regularly update and patch your VoIP systems to address security vulnerabilities that could be utilized in a DoS attack. Using rate limiting can also help by limiting the number of request packets from individual sources, thus minimizing the impact of potential attacks.
Lastly, continuous network monitoring and deviation detection systems will alert you to unusual traffic patterns early, allowing for a quick response to potential threats.
3/ Caller ID Spoofing:
Caller ID Spoofing is a misleading technique where attackers alter the caller ID shown on the recipient’s phone to hide their true identity. As a result, the number and name displayed when you receive a call might not be the actual source of the call.
Attackers use this method to trick you into answering their call by making it appear as though it is coming from a trusted contact or legitimate organization.
This can lead to various forms of social engineering attacks, such as phishing, where the attacker can take out sensitive information from you, or even convince you to perform actions that could compromise your security.
To protect yourself against Caller ID Spoofing, it is essential to be attentive and cautious of unexpected calls. One effective countermeasure is to use authentication mechanisms like Secure Telephone Identity Revisited (STIR) and Signature-based Handling of Asserted Information Using Tokens (SHAKEN). These protocols assist in confirming the authenticity of caller ID information.
Additionally, consider employing call-blocking technologies that can screen and identify suspicious calls. Always verify the authenticity of the caller by calling back on a known number, especially if the request involves sensitive information or financial transactions.
Regularly updating your VoIP system and educating employees about the risks and identification techniques for manipulated calls can further enhance your defense against this threat.
4/ Man-in-the-Middle (MITM) Attacks:
A Man-in-the-Middle (MitM) attack represents a significant danger to VoIP security. This type of attack involves an unauthorized party quietly catching and forwarding messages between two communicating parties, thereby leading them to believe they are in direct communication with each other.
In the context of VoIP systems, this means that an eavesdropper can intercept your conversations, potentially getting access to sensitive information such as passwords, confidential data, and private communications.
According to a report over 50% of MITM attacks in 2022 targeted sensitive information like login credentials and banking data.
To protect your VoIP systems from MitM attacks, you need to implement end-to-end encryption to ensure that your conversations remain confidential, from initiation to termination.
Use secure protocols such as TLS (Transport Layer Security) and SRTP (Secure Real-time Transport Protocol) to encrypt the data being transmitted.
Ensure your network is provided with reliable IDS (Intrusion Detection Systems) to detect and block unusual activities or unauthorized access attempts.
Regularly update and patch your VoIP software and hardware to protect against vulnerabilities that attackers can exploit.
5/ Malware and Viruses:
When it comes to your VoIP systems, another key issue you need to be aware of is malware and viruses. These harmful programs can breach your network, causing significant disruptions and presenting critical security risks.
The forms of malware can vary, including spyware, ransomware, and trojans, each used to manipulate system gaps within your systems.
Once it is inside your VoIP system, malware can steal sensitive information, monitor your communications, or lock you out of your network until a demand is paid.
To secure against malware and viruses, you must utilize dependable antivirus and anti-malware software. Regularly scanning your system for threats can help detect and eliminate any malicious software before it can cause significant damage. Additionally, keep your software up to date to secure your system against the newest threats.
You should also be careful when downloading files and applications from different sources. Always rely on trusted sources and ensure that you verify the legitimacy of any emails and attachments before accessing them.
Additionally, implementing strong firewalls and breach detection systems can help monitor and block suspicious activities in your network.
6/ Phishing and Vishing (Voice Phishing):
Phishing and fishing (voice phishing) are two of the most common tactics cybercriminals use to mislead individuals and get unauthorized access to sensitive information.
In the past two years, vishing attacks have increased, with a significant 40% rise in those targeting senior citizens.
As you manage your VoIP systems, it is crucial to understand and reduce these threats to ensure the security and confidentiality of your communications.
Phishing typically involves fraudulent emails or messages designed to look like they come from trusted and legitimate sources.
These messages usually include links to fraudulent websites that capture users’ login credentials, financial details, or personal data.
You might receive an email that looks like it’s from a trusted contact or institution, urging you to enter your information on a fake site, which attackers can then exploit.
Vishing operates with similar objectives but operates through voice calls rather than emails or text messages to trick individuals.
You could receive a phone call from someone pretending to be a representative of a tech support company or another reputable organization, attempting to persuade you to reveal sensitive information like account numbers or passwords.
Attackers often use caller ID spoofing techniques (discussed above) to make their calls appear legitimate, increasing the chances that you will be tricked into their schemes.
To protect yourself from phishing and fishing, always verify the identity of the sender or caller before providing any information.
Always remain cautious when asked to provide personal or financial information, particularly if the request appears to be urgent or intimidating.
Apply powerful email filtering solutions to identify and block phishing attempts, and consider enabling Multi-Factor Authentication (MFA) to add an extra layer of security to your accounts.
7/ Signal Protocol Attacks:
Signal protocol attacks present a serious risk to the confidentiality of your VoIP communications. The Signal protocol, commonly used for securing voice and messaging services, provides end-to-end encryption to protect conversations from eavesdropping.
However, attackers may still attempt to manipulate weak points within the implementation of this protocol to intercept or manipulate your communications.
To protect your VoIP systems from Signal protocol attacks, you must first ensure that you are using up-to-date software versions that incorporate the latest security patches. This is crucial as developers frequently release updates to fix known flaws that attackers could exploit.
Additionally, it’s important to implement strong authentication mechanisms and utilize strong encryption keys, to protect the system against unauthorized access. Make sure to configure your VoIP system to use strong, unique keys that are regularly switched to enhance security.
Regularly auditing and monitoring your VoIP traffic can also help you identify any unusual activities that might indicate an ongoing attack.
8/ VOMIT:
VOMIT (Voice Over Misconfigured Internet Telephones) is an attack technique that takes advantage of improperly set up VoIP systems. In essence, this attack captures VoIP traffic and converts it into an audio format, allowing unauthorized parties to listen in on your communications.
Despite the advancedness of current encryption protocols, VOMIT attacks can happen when your VoIP system is not properly set up or when security configurations are loose.
To protect against VOMIT attacks, you must ensure your VoIP systems are correctly set up. Begin by using secure and properly set up VoIP routers and firewalls to protect your VoIP networks from unauthorized access.
Implement end-to-end encryption to ensure that even if VoIP packets are intercepted, they cannot be easily converted or understood.
9/ SPIT:
SPIT, short for Spamming Over Internet Telephony, is a type of abuse that involves the mass sending of unapproved voice messages over VoIP systems.
Similar to email spam, these unwanted communications can flood your VoIP network, leading to reduced system performance.
Attackers often use SPIT techniques to disrupt your operations, conduct phishing scams, or simply overload your communication systems with a large volume of junk calls.
To protect your VoIP network from SPIT attacks, you need to implement anti-spam measures. Start by setting up your VoIP systems to filter and block suspicious or known sources of spam calls.
Ensure that your signaling protocols include strong authentication mechanisms to verify the legitimacy of incoming calls. Additionally, incorporating real-time blacklists and anti-spam services can help identify and block spam calls before they reach your users.
Regularly monitoring your VoIP traffic for unusual patterns is critical. By keeping an eye on unusual spikes in call volume or unfamiliar caller IDs, you can quickly identify potential SPIT attacks and take corrective actions.
10/ Call tempering:
Call tampering is another critical security threat within VoIP systems where an attacker interferes with the call setup process to manipulate or disrupt ongoing communications.
When tampering occurs, it can result in various malicious outcomes, such as dropped calls, altered call destinations, or even the injection of unwanted audio streams into your conversations.
This type of attack can severely impact the reliability and privacy of your communications, leading to potential data breaches and operational disruptions.
To secure against call tampering, it is essential to implement all-inclusive security measures across your VoIP infrastructure. First, ensure that all VoIP-related traffic is encrypted using
reliable protocols so that even if intercepted, the data remains unreadable. Secure your signaling protocols by deploying strong authentication and reliability checks to verify the authenticity and accuracy of all signaling messages.
Additionally, consider network segmentation to separate your VoIP traffic from other network areas, minimizing the risk of undetected tampering.
List of most secure VoIP
VoIP Providers | Security Features | Pricing Plans |
RingCentral | End-to-end encryption Multi-factor authentication Secure voice and data traffic | Core: $30/user/month - Advanced: $35/user/month - Ultra: $45/user/month - |
8x8 | TLS/SRTP encryption Real-time fraud detection Secure SIP connections | X2: $12/user/month X4: $57user/month |
Vonage | Secure voice over IP - TLS and SRTP encryption - Data center security - Call monitoring | Mobile: $13.99/user/month - Premium: $20.99/user/month - Advanced: $27.99/user/month |
Nextiva | Encrypted communications Secure data centers Multi-layer authentication | Essential: $25.95/user/month - Professional: $30.95/user/month Enterprise: $40.95/user/month |
What are the security considerations when using mobile VoIP services
When utilizing mobile VoIP services, it is crucial to address specific security considerations to ensure the safety and integrity of your communications:
- Device Security: Ensure that all mobile devices used for VoIP are secured with strong passwords and encryption. Regularly update the device’s operating system and VoIP applications to mitigate vulnerabilities.
- Network Security: Avoid using unsecured public Wi-Fi networks for VoIP communications. Instead, utilize Virtual Private Networks (VPNs) to ensure your data transmissions are encrypted and secure, even on potentially unsafe networks.
- App Permissions: Carefully review and limit the permissions granted to VoIP applications on mobile devices. Only allow necessary access such as the microphone and contacts, and deny permissions that do not align with the app’s core functions.
- Encryption: Implement comprehensive end-to-end encryption throughout all VoIP interactions to ensure the privacy of voice communications. Ensure that both the VoIP service and the mobile app support strong encryption standards.
- Two-Factor Authentication (2FA): Enable two-factor authentication on your VoIP accounts to enhance security and provide an extra layer of protection. This extra security layer ensures that even if login credentials are stolen, unauthorized access is effectively prevented.
- Monitoring and Logging: Ensure continuous monitoring and logging of VoIP traffic on mobile devices. Regularly review logs to identify any unusual activities or potential security breaches.
Why is VoIP considered to be a descriptive technology?
One of the most prominent reasons VoIP is disruptive is its potential for significant cost savings.
Unlike traditional Public Switched Telephone Network (PSTN) services, which incur charges based on distance and duration, VoIP allows unlimited calls over the Internet at a lower cost.
According to a report, businesses that switch to VoIP save an average of 50-75% on communication expenses.
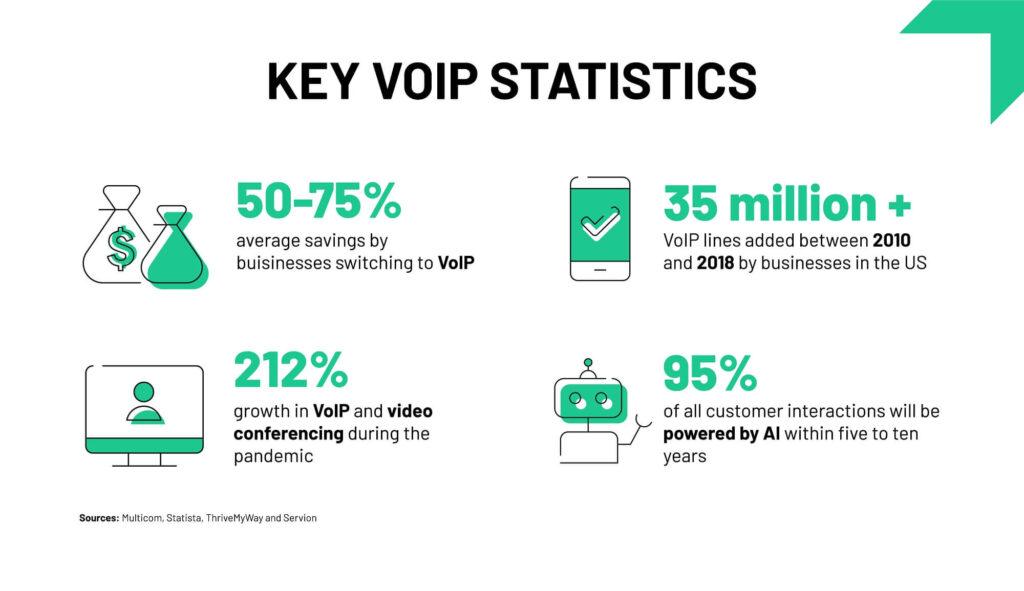
This cost efficiency makes VoIP particularly better for small to mid-sized enterprises that need to manage tight budgets.
VoIP systems also offer superior scalability compared to traditional phone systems. Adding new users is easy and requires no physical infrastructure such as additional phone lines.
Furthermore, VoIP integrates with other technologies, enhancing its functionality and making it highly adaptable to new business needs. Features such as video conferencing, virtual phone numbers, call recording, and voice-to-email become easily accessible through unified communication platforms.
Lastly, VoIP offers improved reliability and flexibility. Physical line damage or local network outages can affect traditional telephony systems. In comparison, VoIP systems can utilize backup and failover protocols to ensure continuous service.
Related Reading:
Frequently Asked Question
Q1) What is the biggest security risk facing VoIP?
Ans: The biggest security risk facing VoIP is the susceptibility to cyber-attacks such as phishing, eavesdropping, and denial-of-service (DoS) attacks. VoIP networks rely on internet connectivity, making them vulnerable to various online threats.
Q2) What are the vulnerabilities exist in VoIP?
Ans: Common vulnerabilities in VoIP include insecure network configurations, weak authentication mechanisms, and a lack of end-to-end encryption. Poorly secured VoIP endpoints, such as phones and softphones, can be easily targeted by attackers to eavesdrop on conversations or execute harmful activities.
Q3) What security risk is most associated with the proposed VoIP system?
Ans: The security risk most commonly associated with a proposed VoIP system is eavesdropping and unauthorized interception of communication. VoIP systems depend on internet connectivity, making them open to cyberattacks utilizing network vulnerabilities.
Q4) How safe is VoIP calling?
Ans: VoIP calling can be safe when appropriate security measures are implemented. Key security practices include using strong encryption protocols to protect voice data, enforcing multi-factor authentication to ensure only authorized users access the system, and configuring networks securely to stop unauthorized intrusions.
Q5) Can a VoIP landline be hacked?
Ans: Yes, a VoIP landline can be hacked if it is not secured properly. As VoIP systems transmit voice data over the internet, they are exposed to various cyber threats similar to other internet-based technologies. Hackers can utilize weaknesses such as weak passwords, unsecured network configurations, outdated software, and ineffective encryption protocols to get unauthorized access.
Q6) What are the three of the most common voice-over IP VoIP problems?
Ans: Three of the most common VoIP problems include call quality issues, latency, and security vulnerabilities.
Q7) Which is more secure VoIP or cell phone?
Ans: The security of VoIP versus cell phone communications largely depends on the specific implementations and security measures in place for each system. VoIP can be considerably secure when strong security protocols are implemented, such as strong encryption, multi-factor authentication, and continuous network monitoring. On the other hand, cell phone communications are generally secured through cellular network encryption technologies, which provide a baseline level of security. However, cell phones are also vulnerable to threats such as SIM card swapping, man-in-the-middle attacks, and exploitation of software vulnerabilities.

